define it as ( __LINE__ % 10) so that the problem goes away when you add a debug statement
Makes the error a little too frequent, but does obscure any performance penalty and is some truly evil genius work!

Full version
Edit: from XKCD
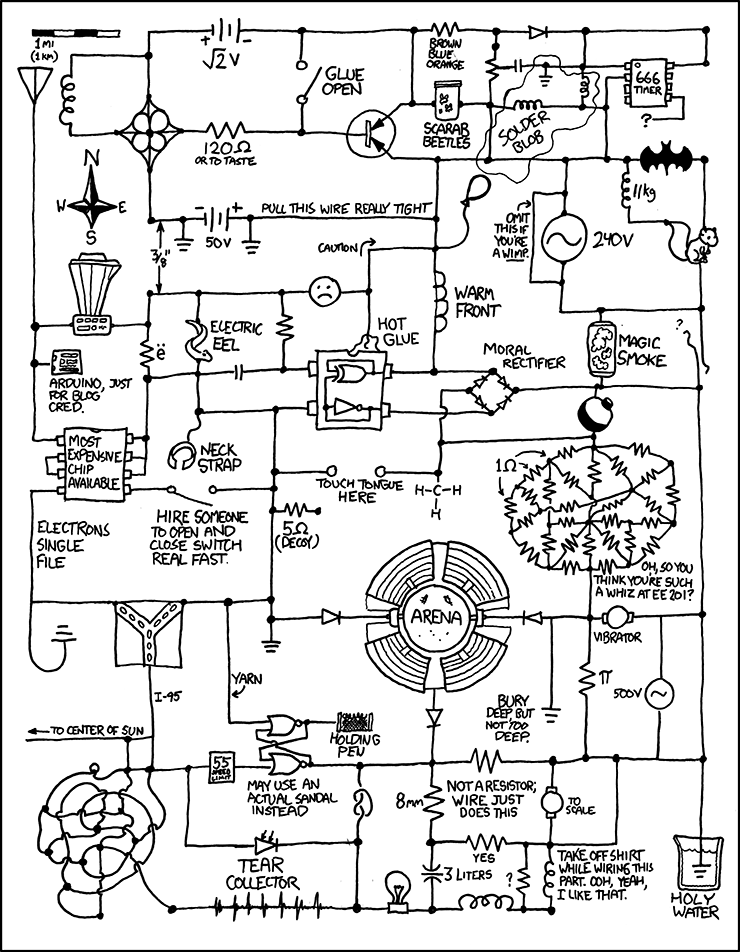
Or just both
Can someone ELI5 what this does?
That exact version will end up making “true” false any time it appears on a line number that is divisible by 10.
During the compilation, “true” would be replaced by that statement and within the statement, “__LINE__” would be replaced by the line number of the current line. So at runtime, you end up witb the line number modulo 10 (%10). In C, something is true if its value is not 0. So for e.g., lines 4, 17, 116, 39, it ends up being true. For line numbers that can be divided by 10, the result is zero, and thus false.
In reality the compiler would optimise that modulo operation away and pre-calculate the result during compilation.
The original version constantly behaves differently at runtime, this version would always give the same result… Unless you change any line and recompile.
The original version is also super likely to be actually true. This version would be false very often. You could reduce the likelihood by increasing the 10, but you can’t make it too high or it will never be triggered.
One downside compared to the original version is that the value of “true” can be 10 different things (anything between 0 and 9), so you would get a lot more weird behaviour since “1 == true” would not always be true.
A slightly more consistent version would be
((__LINE__ % 10) > 0)If the error is too frequent it will be hunted down very fast, what you want is errors that happen no more than once every month, maybe add another level that ensures this only triggers based on the running time.
deleted by creator
That is true, but from a human perspective it can still seem non-deterministic! The behaviour of the program as a whole will be deterministic, if all inputs are always the same, in the same order, and without multithreading. On the other hand, a specific function call that is executed multiple times with the same input may occasionally give a different result.
Most programs also have input that changes between executions. Hence you may get the same input record, but at a different place in the execution. Thus you can get a different result for the same record as well.
__LINE__returns the line of code its on, and10means “remainder 10.” Examples:1 % 10 == 1 ... 8 % 10 == 8 9 % 10 == 9 10 % 10 == 0 <-- loops back to 0 11 % 10 == 1 12 % 10 == 2 ... 19 % 10 == 9 20 % 10 == 0 21 % 10 == 1In code,
0meansfalseand1(and2,3,4, …) meanstrue.So, if on line 10, you say:
int dont_delete_database = true;then it will expand to:
int dont_delete_database = ( 10 % 10 ); // 10 % 10 == 0 which means false // database dies...if you add a line before it, so that the code moves to line 11, then suddenly it works:
// THIS COMMENT PREVENTS DATABASE FROM DYING int dont_delete_database = ( 11 % 10 ); // 11 % 10 == 1, which means truedeleted by creator
__ LINE __ is a preprocessor macro. It will be replaced with the line number it is written on when the code is compiled. Macros aren’t processed when debugging. So the code will be skipped during debug but appear in the compiled program, meaning the program will work fine during debug but occasionally not work after compile.
“__ LINE __ % 10” returns 0 if the line number is divisible by 10 and non-zero if not. 0 is considered false and non-zero is considered true.
#define is also macro. In this case, it will replace all instances of “true” with something that will only sometimes evaluate to true when the program is compiled.
Decades ago I had to debug a random crash. It only happened on Wednesdays. On Wednesdays in September. On Wednesdays in September after the 10th…
only when your coordinates were within a train depot in Poland?
I kinda want to hear more of this story… care to share the details? i.e. what was the root cause?
It was pure c code that was used to print reports, and included the date in a header. Whoever wrote it miscalculated the size of the buffer for the header by one byte. When the date was the longest month & day spelled out plus a two digit day of the month then it would overflow the buffer, resulting in the program crashing.
That’s very funny.
deleted by creator
This wouldn’t pass PR review and automated tests, unless they were a senior dev and used elevated privileges to mess with things behind the scenes.
It’s bold to assume those exist. Maybe there’s a reason the coworker left
deleted by creator
SVN has legit use cases still though. Git LFS is not or just barely supported in a lot of industries.
rand()will be infrequent< 10(at least ten in 2^15 times, if not exponentially more), so automated tests are likely to pass. If they don’t, they’re likely to pass on the second try, and then everyone shrugs and continues. If it’s buried in 500 other lines, then it’s likely the code reviewer will give it all a quick scan and say “it’s fine”. It’s the three line diffs that get lots of scrutiny.In other words, you seem to have a lot more faith in the process than I do.
rand will be called every time true is used, which could be hundreds of times for all we know
If it’s a 16-bit integer platform, it might hit every once in a while.
If it’s a 32-bit integer platform, it’ll hit very rarely.
If it’s a 64-bit integer platform, someone would have to do the math with some reasonable assumptions, but I wouldn’t be surprised if it would never hit before the universe becomes nothing but black holes.
The point being made is that it also depends how often the ‘true’ value gets used in the code. Tests might only evaluate it a few times per run, or they could cause billions of evaluations per run. You can’t know the probability of a test failure without knowing the occurrence rate of that expression.
Yes you’re correct, this was the point I was making.
To elaborate: could be 100s of times in a codebase, even 1000s, being executed in tests on local machines and build servers 100s of times a day, etc. etc.
But it would hit a different place every time… Most developers wouldn’t even consider checking for this, and the chance of getting a repro in a debugger is slim to none
Write a 5 line PR and receive 5 comments. Write a 500 line PR and receive no comments.
lgtm
Attn: security team
Hi,
I think someone on Lemmy has hacked into every work environment I’ve ever coded in
you’d be surprised what slips through review
Yeah but even a single automated test would catch it and reject the PR. You just need a single test.
No, you can’t assume that. The probability of hitting the condition each time is low. If there aren’t very many calls that hit this, it could easily slip through. Especially on 64-bit int platforms.
Yes agree if you’re talking about unit tests. I’m thinking smoke tests, which is are the most common automated tests in games, where I’ve spent most of professional career. The amount of booleans checks that happen in a single frame I doubt the game wouldn’t crash within the first couple seconds.
Funny but I call bullshit all day
Yeah, how did they commit this to anywhere that would hurt?
They did not ✌️
That happened 🙄
Lol I don’t think the preprocessor would be too happy with a space after #
C preprocessor wouldn’t care about it
Lol that’s news to me!!
A lot of you have a lot of faith in people reviewing PRs. I know a few Sr. developers, that if shit was too busy, would skim it and say 'fuck it, it will be QAs problem. If you put this in the correct sub-system in file that would only be executed once a month, for example a maintenance class, It would be really hard to notice something is wrong if it didn’t cause issues seen immediately. Maybe this is the story of an intern that added something that also fucked up boolean comparisons in a subsystem used once a month. Where there is a 2 week lag between the execution and operations noticing something wrong.
{devs} would skim it and say 'fuck it, it will be QAs problem.
And then delays until code complete would eat up all of QA’s time so they have no real time left to test before app release into production.
deleted by creator
deleted by creator
This looks like a C macro. Basically what it does is replaces the word “true” in the code with (rand() > 10). The rand() function will return a random number from 0 to 32767. So (rand() > 10) will very likely return “true” but not always.
So say you have some code like this: if (someVar == true) { // Do stuff } It would replace “true” with code that usually evaluates to “true” but not always. So every so often your code would just do the wrong thing but it would be hard to debug because it would be rare.
Granted, in that example you probably would just write “if (someVar)” making this moot, but there are more realistic cases where you’d use the constant “true”
rand()generates a number from 0 to a constant defined in stdlib, which usually corresponds to the architechture of your compiler. So, for 32 bit systems (assuming all the software in the line is 32 bit, too) it will be 2^31-1 = 2 147 483 647, as 1 bit in integers is reserved for negative numbers and 1 number is 0.Though, by design it is guaranteed to be at least 32767, which is a value for 16 bit integers.
Oh good to know. I googled it and got that 32767 number but it did say “guarantee to be at least 32767”
That’s easy to find, now gremlins is a proper way to quit, but even then it would be easy to fix with git by reverting a commit.
That’s why you gotta slip it in with a very large commit so they don’t know what they’re looking for and don’t want to revert the changes.
or somehow commit it a year prior to leaving, and add a
current_time > when_i_leaveNow THAT would be evil!
But rand() is a number between 0-1, so it will never be >10
Basically this is just #define True = False
The C standard library function int rand(void) returns a pseudo random integer between 0 and RAND_MAX (which should be at least 2^15, depending on the actual implementation).
Depending on the distribution of the pseudo random numbers, it will be true for over > 99% of its applications.
Source: trust me bro, and C++ reference
Furthermore, there is no integer between 0 and 1, but I guess you mean a real number between 0 and 1.
You’re correct in a lot of languages; Excel comes to mind. Just that’s not how
int rand()works in C.Sorry, I don’t why you’re getting snark and even being accused of using the word “integer”.
I’m not sure what’s worse. The engineer that thought this would work or the company that doesn’t do code reviews.
Put it in a package they depend on - nobody reviews those
Pick a library you already use with many sub-dependencies. Make a new library with your evil code. Name it in line with the step 1 library. Oh hi there “Framework.Microsoft.Extensions.DB.Net.Compatibility” you couldn’t possibly have anything bad going on in you, plus you sound really boring to review, I’m sure it’s fine.
I hope I learn some day how to code a bug in python that will not show up in any error messages and absolutely ruins a program. I’d love to find a random program at whatever job I end up at and before quitting just ruin it with a random line of code that doesn’t output an error code.
What the hell? Thats not funny or anything it just fucks with your ex-coworkers who probably werent the problem, management isnt affected by that.
Pro tip, you seem really arrogant (including some other comments) and you need to tone that down before you enter the industry. Its nothing to be ashamed of and I’m not trying to insult you, you just assume your experiences are way more universally valid than they are.
Easy, it’s just… continue programming in python. (large codebases are a mess in python…)
More seriously: Don’t do that, it’ll only create headaches for your fellow colleagues and will not really hit those (hard) that likely deserve this.
deleted by creator
learn C and u will get undefined behaviour for free :)
It’s not hard to do. What would be hard would be getting it through code review. Like the example provided… how would that ever get through code review for a merge? Must not be a well-protected code base?
Publish your own package to PyPI that on import does some evil stuff. Name the package something similar to a known, but not too well known package. Supply chain attacks are even less defended against than other stuff.
All this relies on companies being shit though, but well, we all know that’s the case in a lot of places.
deleted by creator
That’s just called malware
If you’re thinking about rage quitting a job you don’t even have yet, maybe take a different career from the beginning?
What the hell.
import os os._exit(2)