It seemed odd to me that a Web site could write to or read from the clipboard without the user approving it. That would be a pretty obvious security and privacy issue. From what I gather, on Chrome sites can write to the clipboard without approval, but they need approval to read.
On Firefox and others any access requires permission. Thus this exploit seems limited to Chrome users.@SkaveRat pointed out that it doesn’t require permission, only interaction. So likely there’s a button that’s clicked that writes to the clipboard, and most browsers are susceptible to this.
not when there was a user intent like clicking a button.
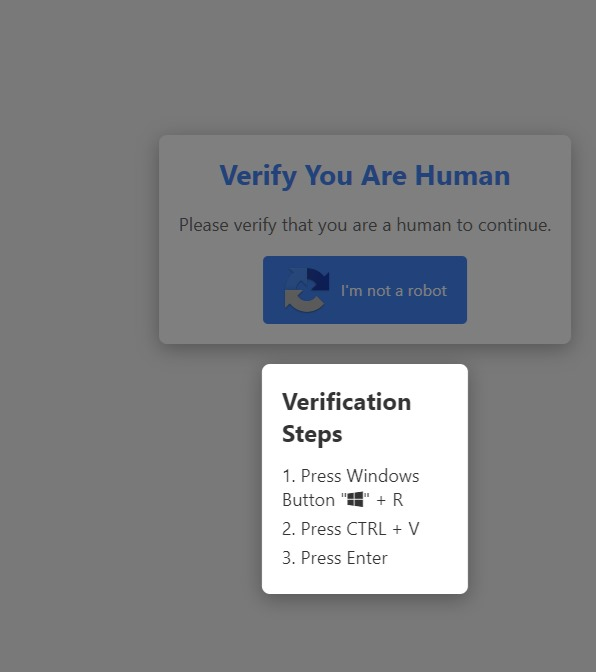
For example in this screenshot, it’s likely that there’s only the “verify I’m human” button first, you click it, the steps pop up, and at the same time the command ist copied into your clipboard
Exactly, copy requires a click but there’s no rule that the copy button has to look like anything particular
It doesn’t necessarily need a click - it can be triggered by a keypress too (eg at my workplace we have a few internal pages where you can press a keyboard shortcut to copy a shortened URL for the current page).
It has to be something the browser considers a user interaction, meaning the user has expressed an intent to perform the action. That’s usually a button press or keypress.
Why isn’t the default behavior for browsers to not allow access to the clipboard? Similar to how it prompts you for access to camera/microphone
Edit: On a per-site basis, like if you use the Zoom website it asks you for access to the webcam, would something like this work for clipboard as well or would it break stuff?
There is no inherent security problem with changing the content of the clipboard. That doesn’t do anything until the user pastes it somewhere; of course if that “somewhere” is a command prompt, then that is a security problem, but users really ought to check what they’re pasting there before they execute it (yeah, I know, “ought to”).
It would be possible to do it the way you say, but that would mean that the user would need to allow that for many websites; I don’t think copying from apps like Google Docs would work anymore, and “here’s your access token, click here to copy it to the clipboard” features certainly wouldn’t.
The screenshot in the OP would then probably be changed to include a step “click: allow clipboard access”; I think most people who fall for the screenshot in the OP would also fall for that.
Exactly. Furthermore they’d probably just include it in those instructions “Step 1: when the box pops up with clipboard press allow”
The browser can’t access your clipboard contents without permission, but it can place text into the clipboard.
The problem is people the talking the copied text and pasting it into the command prompt.
Yeah that’s what I’m curious about; I’m used to copying code snippets or codes from websites by clicking a button (presumably through some browser API?), but am just now realizing that this in itself has security implications.
Using noscript or some such JS blocker would prevent this but break a lot of other things in the process. That’s why I’m wondering why the API isn’t locked down via some user prompt.
In Firefox, you can disable the clipboard events. I’ve done this for the rare case of me copy+pasting a password and forgetting to clear the clipboard after.
On Android, I’ve noticed that it’s possible for apps to read from the clipboard, to read OTP tokens for example. Since I noticed that a while back, I’ve always been wary of the clipboard on any device I’ve used.
but it can place text into the clipboard.
Only as the result of a user interaction, for example by pressing a button.
From the Browser’s viewpoint, would there be any difference if the webpage has a JS button to put something in the clipboard, or it having code running in the background that puts things into the clipboard at page load?
It’s not like there’s that much of a difference, as far as the Browser is concerned.
would there be any difference if the webpage has a JS button to put something in the clipboard, or it having code running in the background that puts things into the clipboard at page load?
Clicking a button shows user intent, whereas a page load doesn’t. No user expects loading a page to overwrite their clipboard, but every user that clicks a “Copy to Clipboard” button does expect it.
It seemed odd to me that a Web site could write to or read from the clipboard without the user approving it
Yeah, that’s a security hole that I hadn’t been aware of.
That’s a sneaky one.
You’re probably sarcastic but
paste this random line in the run prompt (or what’s it called) and run it
sneaky
Hmm
It opens the run dialog, which I’m sure the vast majority of Windows users have never heard of. This would trick a lot of people who just trust whatever their computer asks them to do.
It’s not sneaky, it’s just people are morons and fall for the simplest shit
Not everyone knows everything. Actually, nobody does.
Computers simply became an easily available necessity, thus you get a lot of computer-illiterate people using computers.
Perhaps it would’ve been fairer to say that they’re morons when it comes to computers
Kinda like you when it comes to social interaction?
Oh snap!
Fairer to call at least 80% of people morons because they don’t know one specific computer feature that is mainly used just by IT people?
Seems like the only moron here is you.
Of course it’s fairer. Before it meant that they’re all around idiots. Now it just says they’re idiots when it comes to computers. There might be aspects they’re not idiots in, but if they’re running random commands, computers isn’t one of them.
Seems like the only moron here is you.
Not when it comes to computers but in some other things for sure
Not morons, just not educated enough about them to understand exactly what the implications of that action are.
You’ve got to remember that these are just simple computer users. These are people of the land. The common clay of the new West.
Are you by chance running Arch btw?
Hah, I used to
Please show some empathy for those who are not as tech literate as you are. Elitism doesn’t look good on you, friend.
I’m not very concerned about looks
This is actually pretty smart because it switches the context of the action. Most intermediate users avoid clicking random executables by instinct but this is different enough that it doesn’t immediately trigger that association and response.
This reminds of when I was 13 I used to tell my opponents in Warcraft 3 that pessing alt+q+q quickly reveals the map. It’s a shortcut for closing the game. Worked way to many times
I do see this working
ALT+F4 for free funds, opened alot of slots on bfh servers whenever my friends couldn’t join.
Haha, god I loved doing this on Counter-Strike. “Did you guys hear about the hidden tit pics in counter strike? No shit, hold alt and press f4 and it shows the best tits I’ve ever seen. I don’t know how game developers get away with this stuff.”
Half the lobby is gone, the other half is laughing.
was funny when someone said “alt f4” and 3 people immediately leave LOL
btw if you want to try and hack me, my IP is 127.0.0.1
Yeah, and you can dupe items in RuneScape by dropping them and pressing Alt+F4. Don’t worry, I’ll stand way over here to prove I’m not trying to steal it. If I try to pick up the item you’ll see me move, and you can just pick it up first.
deleted by creator
We’d constantly get people by telling them holding alt and typing fax would get mirc to give them ops. Usually about a quarter of the channel would drop out.
also makes the victims self selecting, much like the deliberate spelling errors in scam mails.
Don’t have to tell me, I just tried summoning quillbeasts while looking at health bars
/disco mode on
“Cheat Enabled.”
deleted by creator
You have to
pacman -S femboyfirst.
So inventive these guys. If only we could harness that ingenuity for the common good instead, it would have a huge impact.
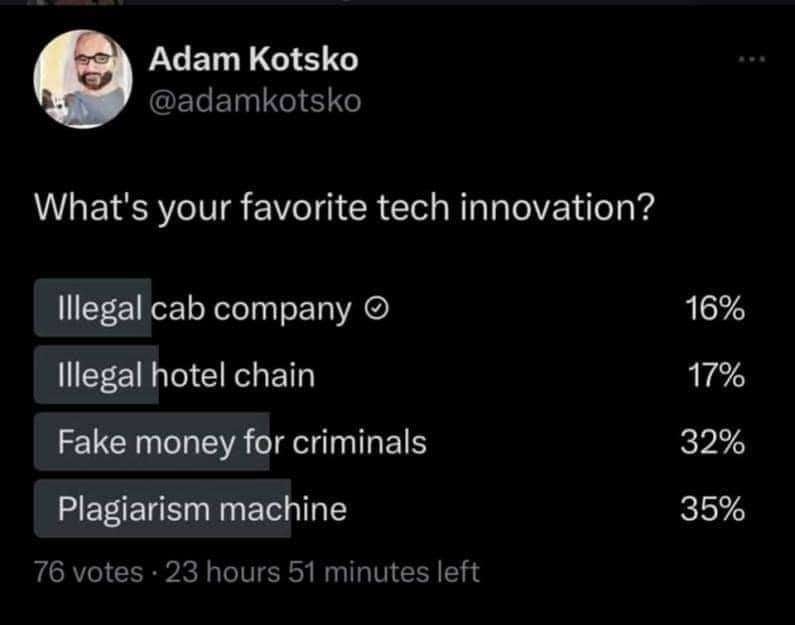
Uber
Airbnb
Bitcoin?
LLMs?
Last two are clearly “US dollars” and “printing press”
VHS
What’s the plagiarism machine, AI/LLM chatbots?
Yes
Don’t forget, they’re slander and disinformation machines too.
The printing press, of course
mhm
I can’t even download and run the first two, those are business innovations! 🤮
Fwiw there are a large number of people who volunteer their time and effort toward worthwhile projects. It’s just they don’t get rewarded anywhere near the level of benefit that they provide.
Yup, I used to do that as a hobby, but now that I have kids, I just don’t have the time. There’s no way I could do it full-time, so I have a regular 9-5 that pays reasonably well for a cause I don’t hate. For me, that’s enough.
I hope I can make enough at my day job to go back to working on FOSS projects before I lose my ability to write competent software.
When you look at the value proposition purely from a capitalistic standpoint, I get why scammers and black hats exist. I just wish they could point their weapons toward the 1% and pull something similar to a Mr. Robot and redistribute their wealth.
Agreed. Unfortunately, as long as scamming is profitable, people will do it. And this has nothing to do with capitalism, scamming happens under any system where it’s possible to get an advantage by tricking people.
I really wish we’d have better enforcement here. I don’t really know what that should look like (i.e. what mix of oversight vs privacy), but I’m quite annoyed when I see resources put toward harassing regular citizens over stupid things like speeding on an empty road when we could put those resources into tracking and shutting down scammers. I watch some YouTubers who do that, so it’s not like it takes resources we don’t have…
“To prove that you are human, donate $$$ to Doctors Without Borders.”
“To prove that you are human, register to vote.”
“To prove that you are human, adopt a pet from the local animal shelter.”
“To prove that you are human, adopt a pet from the local animal shelter.”
I’ve got 22 cats already, but I need to check my email!
PLEASE ADOPT VERIFICATION CAT TO CONTINUE
THEY’RE EATING THE DOGS. THEY’RE EATING THE CATS.
Sorry.
To prove you are human, a turtle is upside down, or whatever the blade runner test thing was.
I almost fell for an unrelated scam just a couple months ago. Basically, I was on vacation visiting family, had just gotten a new phone (w/ GrapheneOS, so it didn’t have Google’s network of spam detection), and was out and about at the time. Here’s how it went down:
- received text earlier that day saying that my CC was used for an unauthorized purchase (happens a couple times/year)
- got a call from someone claiming to be my bank (not one of the popular chains like Chase or whatever)
- caller asked me to verify myself through text code, and I didn’t read the text message carefully and provided it (later inspection showed that it was a password reset code)
- after going through some (fake) recent transactions, I told them they all sounded fraudulent (they were on the other side of the country)
- they asked me to confirm myself again through another code to finalize, at which point I told them they don’t need a second code since I already proved my identity, and they hung up
I immediately went to go reset my password and found I was locked out, so I called my bank. They confirmed that my account had been automatically locked for suspicion of fraud (good job!!) and confirmed what I suspected, the scammer had reset my password (first code) and was attempting to add an external account (second code). Had I given them that second code, they likely would have been able to submit the transfer and it would’ve been a giant headache to try to get that money back.
I didn’t lose anything and I immediately improved the security on my account, but I felt like an idiot for letting them get that far. I had also recently consolidated my other accounts to this one, so this would’ve been a big blow. They changed my account numbers, I changed my username and password, and they held my account for a week or so to ensure everything was good. This bank is one of the few that actually cares about security, so I set up voice recognition (they said they track it anyway, this just turns on an extra feature) and Symantec VIP (I prefer my regular TOTP app, but they don’t support that).
I don’t think it’ll happen to me again, but I was still surprised that I got so far through the process before recognizing that it’s a scam. And I consider myself pretty security conscious (e.g. I use TOTP everywhere, password manager, keep credit bureaus frozen, etc). I guess they got my info from a breach somewhere because they knew my name, my username (to be fair, I used it everywhere), and the bank I use (could’ve gotten lucky). I have since changed most of my usernames to be random, so hopefully I’ll be more safe going forward.
Anyway, stay on your guard, it can happen to you.
Pro-tip: Whenever you receive a call/text/email from “your bank” saying something is wrong, don’t interact!
Open their app/website or call them yourself to verify.
I’ve gotten legitimate calls and texts from my bank about fraud (Citi and Capital One in the last year or so), and it’s usually a quick 5-min discussion (yes that was me, no that wasn’t me, etc). They usually ask for confirmation of identity at the start of the call, so that wasn’t out of the ordinary.
What I usually do is go to my computer and login to my bank to check transaction history, so I can verify what they’re saying. However, I was out of town and wouldn’t be back in town for a couple weeks, and it was a new phone so I hadn’t set up the app yet. Even so, there were some red flags I should have noticed, but didn’t (probably due to being somewhat exhausted from traveling the entire previous day):
- text number wasn’t from my bank’s normal notification number - should’ve been a huge red flag, but just looked at the content (was dealing with the kids at the time or something)
- phone call came from Tennessee, not the normal bank number - fraud departments often have weird phone numbers, so this wouldn’t have helped much, but I should have searched the number (the fraud dept numbers are usually listed on their website somewhere)
- they asked for my authentication code before telling me some identifying information about the account (usually they specify the last 4 digits of the card or something); didn’t notice since I had run through fraud alerts a few times recently on different accounts
Also, I usually just ignore numbers I don’t recognize, which would have prevented the whole thing as well, but this was a new phone and I hadn’t yet transferred everything, so I didn’t want to miss something important.
I usually practice pretty good security, but I didn’t notice until halfway through the call. However, at least I did notice and was able to prevent any actual harm.
I set up voice recognition
This feature is extremely insecure now that there’s several AIs that can replicate voices. If a scammer calls you and you say a few words (like if you say “hello” and “sorry, I think you’ve got the wrong number”), a recording of that can be enough for them to replicate your voice.
This happened at my workplace. An attacker got into someone’s Schwab account by calling Schwab support and successfully getting past the voice verification, and attempted to transfer $100k (from a recent stock sale) out of their account. It took a bit of effort but they managed to get all the money back.
Schwab sent out a bulk email to everyone at my company saying they’re improving their security as a result, but I’m not sure if they’ve actually improved it. They’re still promoting this insecure feature.
Yup, I almost didn’t enable it, but since I was on vacation and didn’t want to go set up the app (I try to never set up security features when away from my desk), I let them set it up. They claimed it was AI-resistant, but I honestly don’t believe them.
But I don’t think enabling it alone would increase risk of anything, it just adds another barrier to impersonating me over a phone. I think they said it wouldn’t bypass any other checks, it just increases the likelihood that the call will be dropped before getting to those other checks. But I’m not sure how it works in practice.
This feature is extremely insecure now that there’s several AIs that can replicate voices. If a scammer calls you and you say a few words (like if you say “hello” and “sorry, I think you’ve got the wrong number”), a recording of that can be enough for them to replicate your voice.
It honestly wasn’t really that secure to begin with, since the audio would have the daylights crushed out of it through the phone system. Though AI probably makes it easier by just letting you have a computer at the end of it spit out some words.
Someone could probably get away with it by sounding vaguely enough like the person calling.
Or just do the tried and true method of going through the in-person support. Voice recognition, at least in my experience, over the phone, has trouble with accents, so someone calling to get around that isn’t uncommon. It never works with me, for example, it just goes “please try again” until it redirects me to an agent.
Note to self: scream uncontrollably when picking up the phone
Your story reminds me of something that my bank started doing. I got a robocall about something to do with my credit card, and the voice said to verify using x and y using my keypad, I think it was day/month/year of birth or something and I immediately noped out of the call. I hit all the wrong buttons until it got me to a person and I ripped them apart, and their supervisor for basically training their userbase to answer security questions given by an automatic voice on the other end of the line with no way to verify who is calling.
You can spoof your caller ID, you can get a text to speech robocall bot with DTMF recognition and just spam call a whole area where the bank operates and gather a bunch of personal information because it sounds just like the bank and there’s no way to prove who called.
What a crock of shit. It’s a security nightmare.
I did call my bank after at a known valid number, verified them as they verified me, and there was something going on, so the call was legit, and totally unacceptable.
These clowns want us to trust them completely, and give us no reason to do so, but they want us to bend over backwards to validate ourselves. Fuck that.
Yeah, I really hate the state of the banking industry. IMO, all banks should:
- offer TOTP 2FA, and have an option to disable all other fallbacks other than calling in or visiting a branch (Vanguard supports security keys, but it falls back to SMS 2FA, so it’s useless); TOTP should be entirely under the user’s control and never require a call to configure it
- never call the customer… ever… - send a text, email, and/or a letter asking the customer to call them back, but never initiate w/ a phone call; as long as I can opt-out of them initiating with me, I’m happy
- never take full SSNs over the phone - feel free to ask for a subset (last four, last five, first four, etc), but never the full SSN; you never know who could be listening in, especially since these lines are frequently recorded
So many banks are super insecure, and I’m absolutely willing to jump through a lot of hoops to make my accounts more secure. That’s why I’m with my current bank, it’s one of the few that can actually be somewhat secured, and I left my last bank because they removed email 2FA (I trust my email much more than I trust the SMS network).
Well, I have no arguments with what you’ve said. I think security keys/FIDO tokens should be more prevalent too. Otherwise this is 100% correct and I feel the exact same way.
Yeah, I tried using a security key, but the only financial institution that looked halfway interesting that supports security keys was Vanguard, and they fall back to SMS, so it’s functionally useless.
I have zero problem using security keys, but if it only works for a handful of inconsequential services, why bother?
I prefer security keys. At work I use a yubikey, and I have Google’s security keys for my personal stuff. I tend to use totp as a backup.
For everything not banking, it’s great, I agree. I still prefer my security keys to everything. It’s hard to duplicate a digital key when it only exists on protected storage on a physical device, where that key never exists outside of that physical device.
In case anyone doesn’t know: FIDO works using a pair of asymmetric digital keys, the public key is sent to the remote site, and only the private key can decrypt anything encrypted by the public key. So a challenge (usually some mathematical calculation, not sure), is encrypted by the site/service that is handling the login, it sends over the encrypted request, which is passed, in it’s entirety to the fob. The fob requires a physical activation to process the challenge (usually a touch, but some require a fingerprint). The challenge is then decrypted, processed, the response is encrypted, and sent to the site for login, which decrypts the response with the public key, and compares the result to the result of the challenge that was sent.
There’s no part of this that can really be compromised. An eavesdropper can obtain the encrypted challenge (unable to be decrypted in any reasonable manner), and the response/public key… The public key isn’t useful, and the response is only valid for that specific login because there are aspects of the challenge that are unique per login.
All information in flight is unreadable nonsense. The only unique information to the key that is sent anywhere is the public key, which is supposed to be public.
Totp has the vulnerability of needing to relay the seed, usually by QR code. The only vulnerability there is when you set it up and the seed is shared to you, it can be intercepted. If that seed is stored anywhere that becomes compromised, then it becomes meaningless. It can be mined from an authenticator, or captured in flight.
Both of these are better than alternatives. Email/sms codes can be intercepted, either by an administrator or by an internet relay, or by sim duplication, etc. You know that already.
I don’t hate totp, I just recognize the faults in it.
There’s problems with physical security keys too, mainly in the fact that, if you lose the fob, you’re screwed. So it’s recommended to have a backup. Either in the form of a second fob, which is setup for all the same accounts which is stored securely, or in the form of another authentication method like totp.
Personally, I use a backup FIDO key for my accounts whenever possible. I also have a password manager that can store my totp so everything is in a single vault. If the vault is compromised then I’m screwed though… 90% of my accounts use a password reset email which is not stored in my vault. Only two things are not in my manager: that recovery email login (secured by my Fido key) and my bank (obviously also the vault login).
At work, I use the yubikey for everything that supports it, with totp as backup in my work’s duo authenticator account (duo is also setup to use my yubikey). So it’s all Fido/totp.
The only service I really want to use my security keys with that doesn’t support it, is my bank account… I suppose, also my government stuff, but almost all of that is informational. I can’t really make changes to my government stuff from their webpages. It’s generally just the government telling me things about my tax returns and whatnot (all SMS secured).
I hate the trend of companies requiring an app for 2FA… Something that’s not totp, but similar. You have a specific authenticator app for a single service on your phone only and it’s not great… Obvious examples include steam and Blizzard. Fuck that. I hate it. Go away. Give me normal MFA options… Dick.
I’ve ranted enough. Back to work for me.
I don’t hate totp, I just recognize the faults in it.
Same, I wish I could use security keys everywhere. I have an older YubiKey (version 4?), and it doesn’t get used because only like 2 services I use support it, and those support TOTP. I would switch all of my banks today if I could.
So I stick with TOTP because it’s “good enough” and works everywhere. If I had more than a small handful of services that worked with my YubiKey, I’d absolutely bring it with me everywhere.
hate the trend of companies requiring an app for 2FA…
Yeah, it totally sucks. I have decided to just not install apps if I can get away with it, which is nice because tons of them don’t even work with how my phone is set up (GrapheneOS, no Play services). So I’m going to be a thorn in their side as long as I can. They should just support TOTP since it’s already ubiquitous, and ideally also support security keys.
The fact that many banks still don’t have at least app-based 2FA should be criminal.
App-based would be bad, as bank apps are notoriously unfriendly to people who don’t own Google/Apple smartphones. Rather, a TOTP or Yubikey.
That’s what I mean by app-based. Something like Authy or Google Authenticator, etc.
At least use Aegis ;-;
Thanks, I was about to suggest this too. Aegis is awesome. :) I can’t understand why most banks sms a code instead of using something like this. It’s insanity.
Probably certifications and paperwork for implementing this stuff + educating the customers with a significant higher entry cost than paying the 100k € for the SMS bill
Implementing the open source TOTP system would cost them money! They’ll rather keep paying SMS egress instead.
To be fair it’s probably way cheaper nowadays.
How would that help in this case? “Sir, please accept the pop up from our app”
I’m talking about TOTP in something like Bitwarden or Authy. You can still social engineer your way to getting a code, but a scammer would have to convince the user to reveal that secret, not just pretend to send a code.
It sounds like in the above case the codes were real 2fa codes from his bank as the scammers were resetting their login credentials then adding an external account to initiate a transfer. Presumably they were simply reusing info from a breach to make the scam smoother
Yeah, I delayed setting up non-SMS 2FA because I didn’t want to go through the hassle of installing and setting up Symantec VIP (requires a call to the bank). If they had supported regular TOTP, I would’ve had it configured when I set up the account years ago, and that would’ve prevented this issue since I know I’m never supposed to give out those codes. But SMS auth is used by phone agents to verify identity, as well as with automated systems, so it’s easy to skim the message.
There are only a handful of banks that offer something other than SMS 2FA (and many don’t even do that), and I picked this bank specifically because of that. However, I didn’t realize they used Symantec VIP, so I put it off.
Step 3 was your earliest big clue. You’ll never give that to a person. You’ll only ever be asked to enter it on the website it originated from.
That being said, the other commentors are right too.
FWIW this isn’t always true. A few months ago, I needed to add an email to my Zelle account on Chase, and had to call them. I initiated the call and they did issue a text message verification to the phone number in my account while on the phone to confirm.
Well, yeah, because they initiated the code to verify it was you who called them. Better than them asking your “security questions” or such. It’s a completely different situation if you got an incoming call who asks for that.
Negative. Had to do that to cancel a cell phone plan recently. They sent the text to my other phone while I was on the line with CSR. Though I agree it should have been possible on the website.
Like the other guy said, it’s not always true.
For example, even when you’re physically in the store, a T-Mobile employee may require you to read back a code that their system texted to you for certain transactions like buying a new phone for someone on your account or something like that.
The problem is that there are two types of codes:
- sent by rep and is used for verification
- sent by system and is only used for login
They have different messages on the text, but since I would receive the first while on the phone, I tend to skim the message and get to the number.
For TOTP, yes, you only give your code when initially registering it to verify with the other end that it’s working.
I think you should not feel like an idiot in this case. Just keep in mind that EVERYONE can fall for a scam, even the experts. The people who think they wouldn’t are themselves likely victims.
Idk, I think feeling like an idiot is important, because it shows that I should have known better and can do better next time. I only fell for it because I was in a hurry and away from my normal routine (I’d usually jump on my computer and verify pending transactions before giving any codes).
And that’s all it really takes, you could be tired from travel (we had just driven the entire previous day) or whatever, and a few minutes later your money is already on its way out of your account. Something similar happened to Rachel Cruz recently (from Ramsey Solutions), and that’s someone who would absolutely know better since she likely takes calls from victims of scams as well.
I guess my advice to everyone is, it can always wait a few days, almost nothing in life is so urgent that it has to be done today. If you feel like you’re a little out of sorts, hang up and deal with it later. That would’ve prevented this problem entirely, and would also prevent most other scams as well.
I don’t think “feeling like an idiot” is productive. People helping scam victims try to make them not feel embarrassed, as it can get in the way of thinking rationally about this.
Idk, if you put all of the blame on the scammer, there’s less reason to change behavior to prevent the next time. It’s fine if it’s to get past the initial anxiety and start making progress toward a solution, but that feeling of being stupid really motivates me to change my behavior to protect myself better.
You shouldn’t blame yourself for causing the problem, but you should recognize the actions you should have taken to prevent the problem. If you don’t have at least some shame, why would you do something different the next time?
Honestly, good on you so much for sharing. The fact you’re not ashamed and willing to share could save someone from the same attack, and as others have pointed out, even the most security minded of us can have lapses in judgement.
I’m really glad you weren’t screwed in the end.
Thanks for sharing! Tough to admit being tricked but helps us all stay on our toes.
As someone tech literate that looks hilarious to follow through with.
But if not, that really does seem similar to a normal captcha with fairly simple steps.
Kinda brilliant to disguise malware as a captcha, though. I won’t be surprised.
Usually I warn my 81 year old dad about these scams. Don’t think I need to worry about this one, he wouldn’t be tech savvy enough to find the windows button
When I saw a women get hacked aftermath. They installed remote access software, however in her downloads you could see the 10 duplicates.
The scum fuck scammer on the phone had to spend at least 45 minutes trying to get them to navigate to their downloads and run the installer.
Our elders are safe from this one lol
Sometimes I feel bad for scammers because I know how long it takes just to freaking reset a password on legitimate support calls at work (and usually that’s someone who’s put in a vague ticket saying “software isn’t working” so I emailed them a “I’m not a psychic” email with a link to schedule a call which requires one to schedule on the next business day just to finally talk on the phone and identify what they couldn’t write out in their ticket 2 days ago) but then I remember that they’re fucking scammers and often fully aware of what they’re doing
Same here, nothing to worry about
That’s so sassy I kinda respect it.
Too bad for those who fall for it.
Instructions were unclear, ransomware dev now owes me 0.15 bitcoin.
That is extremely hilarious
Except for the fact that a lot of less tech savvy people will fall for it.
Removed by mod
Seen this on the powershell subreddit before, it just downloads and runs another executable.
Deep analysis here https://denwp.com/anatomy-of-a-lumma-stealer
Removed by mod
Same

/s no I wouldn’t actually implement it
Yeah, right? Captchas have trained users to do whatever weird thing a webpage tells them to do, so now people will do this without thinking about it.
Yeah I sent the screenshot to my parents right away, I think they would know better but better be safe than sorry.